


|

|

|
 |

|

|

|
 |
 |
 |
||||

|

|

|
 |

|

|

|
 |
|
|
|
Public members in dll libraries are advisedly reserved from obfuscation because they are intended to be used in external assembly code. If you are sure some of public members are not to be accessed from outside, you may want to obfuscate them. |
|
|
Let's try to write a simple command-line application and then obfuscate it. The following console programs are the VB.NET and C# version of the "Hello World!" program, which displays the string "Hello World!" Actually it is not the traditional "Hello World!" and it displays in addition today's date and current time. We have added couple of private variables to see what happen when we obfuscate them. |
|
VB .NET
|
|
C#
|
|
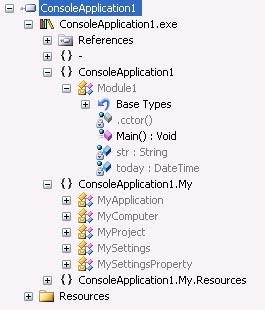
You can see four highlighted members' names. Two are private variables' names today and str. Module1 is name of the class. Main is name of method that is single method in the simple class. |
|
IL
|
|
Everything looks pretty obvious and understandable in the IL script. Is not it? Right, it is hard to figure out the IL code for us more mortals. So if you are now guessing your .NET source code will be accessible only to a small circle of technical folks who actually know IL Assembly Language, think again. You can take this step further and actually recreate the source code by using some much sophisticated decompilers. These decompilation tools can decompile a .NET assembly directly back to a high level language like C#, VB .NET, or C++. |
|
|
Ok, we are ready to obfuscate the sample ConsoleApplication1.exe executable by using Skater .NET Obfuscator. Open the exe file in Skater Obfuscator. In the Obfuscator interface go to Options tab and select 'Alpha-Numeric characters' under 'Naming Conventions'. Choose all Private and all Public members obfuscation mode. |
|
IL
|
|
Skater .NET Obfuscator just replaced member names with alpha-numeric combinations that makes harder to understand the code. However it is not so big trick and every Obfuscator can do that. Everyone can replace the alpha-numeric char combinations with some eye-friendly names. Moreover, by using ILasm.exe (one more .NET Framework SDK assembler utility that allows you to compile IL code back into an executable) we can easily recompile the obfuscated IL output and it will work without problems. |
|
IL
|
|
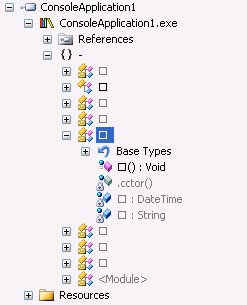
Sure, the presented above IL code can not be compiled or the compiled executable will not work well. As you can see all member names has the same single '?' character representation. We can get the result by using Skater .NET Obfuscator special settings. In the Obfuscator interface go to Options tab and select '?' characters under 'Naming Conventions'. |
|
|
The member names obfuscation is the very first essential step of .NET assembly obfuscation. You need to apply other Skater .NET Obfuscator methods and algorithms to better secure your .NET apps. |
|
|