|
|
|
|
|
|
|
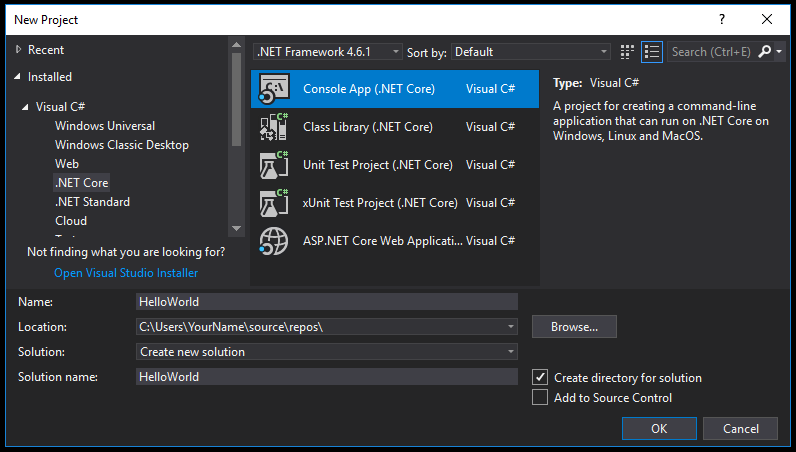
To test how Skater Obfuscator protects .NET Core assemblies open Visual Studio 2020 and create new .NET Core project. |
 |
|
In the Name text box, type "HelloWorld". Select the OK button. |
|
C# Console.Write("Press any key to continue..."); Console.ReadKey(true); |
|
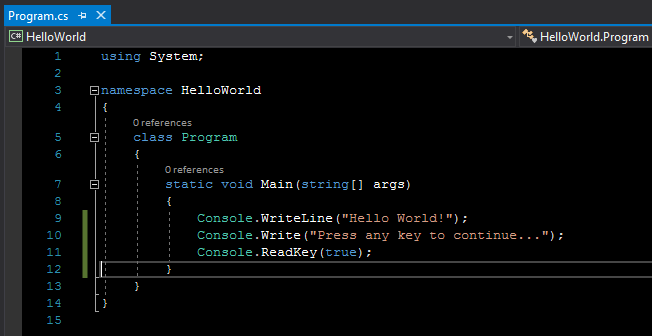
This code prompts the user to press any key and then pauses the program until a key is pressed. You will get the following source code: |
 |
|
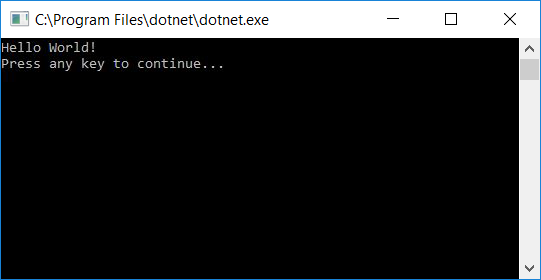
On the menu bar, select Build > Build Solution. This compiles your program into an intermediate language (IL) that's converted into binary code by a just-in-time (JIT) compiler. |
 |
|
Press any key to close the console window. |
|
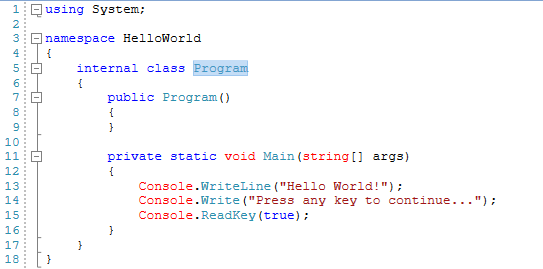
Take a look what we got after the HelloWorld.dll .NET Core app decompilation: |
 |
|
We can see the non-obfuscated "Hello World!" string in the decompiler's interface. Decompilation tools can decompile a .NET assembly directly back to a high level language like C#, VB .NET, or C++. We are ready now to obfuscate the sample HelloWorld.dll .NET Core app by using Skater .NET Obfuscator. In Skater .NET Obfuscator open HelloWorld app. |
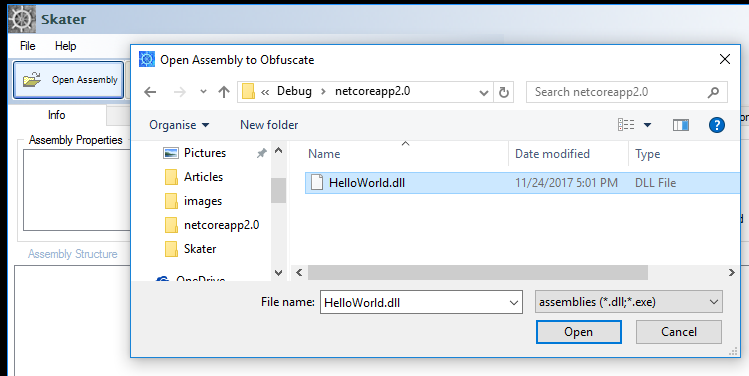 |
|
Skater immediately identifies the HelloWorld.dll is .NET Core assembly: |
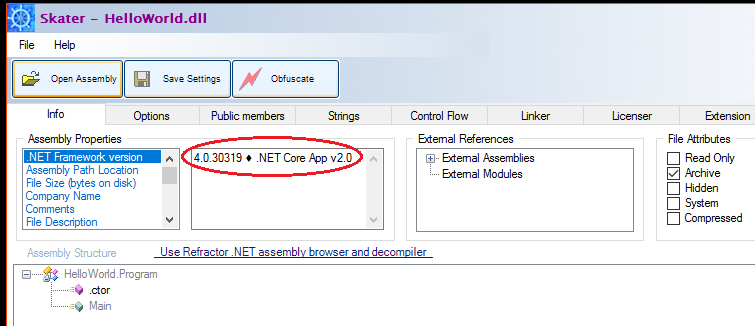 |
|
Now you can adjust HelloWorld.dll app obfuscation settings and run its protection process. |
 |
|
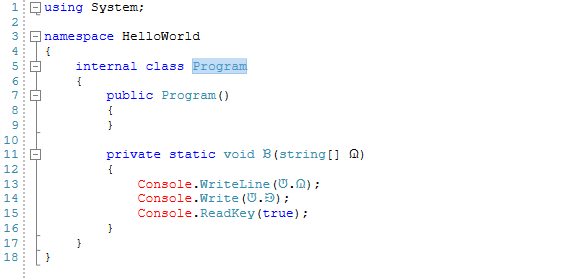
The "Hello World!" string has been allocated by Skater into a public variable then it was encrypted. We can pretty easily spot the encrypted string inside that decompiled script. Should this make it pretty obvious that our code is protected? Is it not simply too easy to decrypt the safe .NET Core source code? Almost. An absolute hacker still can choose a password for the encrypted string and decompile it. As a conclusion, no matter what we do, if our code is placed at the end-user's PC/Mac/Phone, it is not safe. As long as the code is placed at the end-user, all we can do is to make it as unwieldy as possible to get to the original source code, with any luck avoiding most hacker's attempts. |
|
|
|
|
|
|